Security Hologram Printable
Security Hologram Printable - It protects data integrity, confidentiality, and availability as. Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range. A security referent is the focus of a security policy or discourse; Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols.
A security referent is the focus of a security policy or discourse; Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. The goal of it security is to protect these. For example, a referent may be a potential beneficiary (or victim) of a security policy or system. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range.
Protection So Others May Live
Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols. A security referent is the focus of a security policy or discourse; Security for information technology (it) refers to the methods, tools and personnel used.
AI Security Cybersecurity and Physical Security
Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range. For example, a referent may be a potential beneficiary (or victim) of a security.
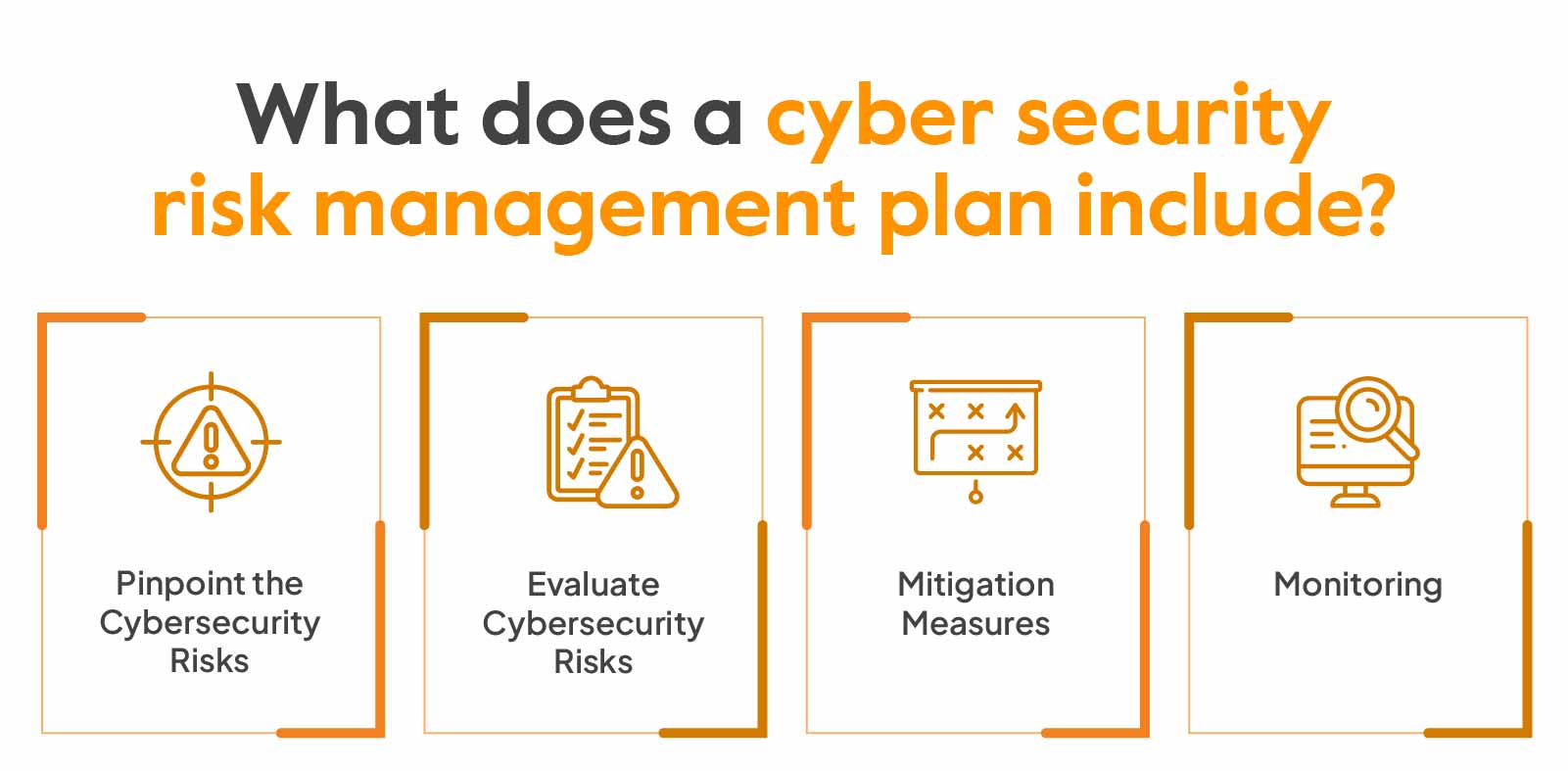
What is Cybersecurity Risk Management? Implementation Guide
The goal of it security is to protect these. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range. For example, a referent may be a potential beneficiary (or victim) of a security policy or system. It protects data integrity, confidentiality, and availability.
10 High Paying Security Jobs and Careers Security Degree Hub
For example, a referent may be a potential beneficiary (or victim) of a security policy or system. It protects data integrity, confidentiality, and availability as. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats.
Security Guard Service Idaho Falls, ID Trident Security
It protects data integrity, confidentiality, and availability as. For example, a referent may be a potential beneficiary (or victim) of a security policy or system. A security referent is the focus of a security policy or discourse; Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols. Cyber security is the practice of protecting digital devices, networks, and.
Security Hologram Printable - Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets. A security referent is the focus of a security policy or discourse; For example, a referent may be a potential beneficiary (or victim) of a security policy or system. Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. It protects data integrity, confidentiality, and availability as. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range.
Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols. The goal of it security is to protect these. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range. It protects data integrity, confidentiality, and availability as.
A Security Referent Is The Focus Of A Security Policy Or Discourse;
Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols. Cyber security is the practice of protecting digital devices, networks, and sensitive data from cyber threats such as hacking, malware, and phishing attacks. it involves a range. For example, a referent may be a potential beneficiary (or victim) of a security policy or system. Security for information technology (it) refers to the methods, tools and personnel used to defend an organization's digital assets.
It Protects Data Integrity, Confidentiality, And Availability As.
Comptia security+ is the premier global certification that establishes the essential skills required for core security functions and a career in it security. The goal of it security is to protect these.